For the past twenty years, one of the main pieces of advice our industry gave to people regarding their email was "don't open attachments from people you don't know." But what if your JOB is opening attachments from people you don't know?
On August 1st, the US Attorney for the Western District of Washington, Annette Hayes, and the FBI Seattle Special Agent in Charge, Jay Tabb, along with main Justice's head of the Computer Crimes and Intellectual Property Section (CCIPS), Deputy Attorney General Downing, gave a fascinating press conference about the FIN7 or Carbanak Group case. (The link shows the 31 minute press conference on YouTube, where closed captioning is available.)
As AG Downing explained it, the FIN7 group would use a combination of emails and telephone calls to encourage people involved in catering or group reservations to open their malicious emails. Imagine that your job is booking hotel rooms for group travel, or handling large catering deliveries for business meetings from your restaurant. A new potential customer calls and says "I'd like to book forty hotel rooms for our sports team that is coming to play in a tournament in your town next month. What email should I send the details to?" Or "We're having an event at my office and need to order lunch for sixty people. I know that I could use the online order form, but would you mind if I just sent you an email with the details?" (I've done the latter myself when ordering FIFTY pizzas from Dominos!)
What sales person is NOT GOING TO OPEN THAT ATTACHMENT? Right. Every single one will do so! Here's the flow of the attack that was shared at the Press Conference:
Brian Krebs was one of the journalists who has written extensively about Joker's Stash. In this image from his blog post "Will the Real Joker's Stash Come Forward", he shares an image of the card "base" "FIRETIGERRR" associated with the Sonic Drive-In databreach, showing a screenshot of the September 26, 2017 announcement on Joker's Stash about the availability of 5 million credit cards:
On August 1st, the US Attorney for the Western District of Washington, Annette Hayes, and the FBI Seattle Special Agent in Charge, Jay Tabb, along with main Justice's head of the Computer Crimes and Intellectual Property Section (CCIPS), Deputy Attorney General Downing, gave a fascinating press conference about the FIN7 or Carbanak Group case. (The link shows the 31 minute press conference on YouTube, where closed captioning is available.)
As AG Downing explained it, the FIN7 group would use a combination of emails and telephone calls to encourage people involved in catering or group reservations to open their malicious emails. Imagine that your job is booking hotel rooms for group travel, or handling large catering deliveries for business meetings from your restaurant. A new potential customer calls and says "I'd like to book forty hotel rooms for our sports team that is coming to play in a tournament in your town next month. What email should I send the details to?" Or "We're having an event at my office and need to order lunch for sixty people. I know that I could use the online order form, but would you mind if I just sent you an email with the details?" (I've done the latter myself when ordering FIFTY pizzas from Dominos!)
What sales person is NOT GOING TO OPEN THAT ATTACHMENT? Right. Every single one will do so! Here's the flow of the attack that was shared at the Press Conference:
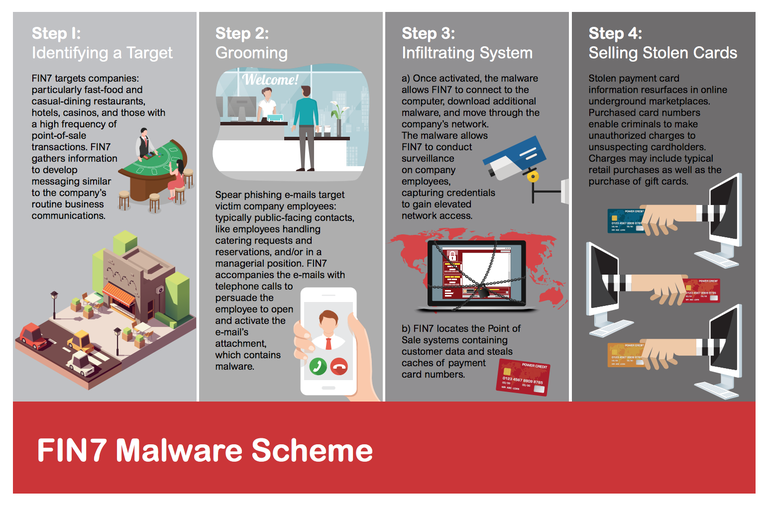 |
| (Image from FBI Seattle FBI Office) |
Although the schemes I suggested sound complex, some of the emails shared during the press conference were quite simple:
 |
| Spear-phishing Email Image from justice.gov |
 |
| Spear-phishing Email Image from justice.gov |
Three criminals were arrested in this scheme, each on their own indictment. The first two were actually arrested in January 2018, but their arrest and information about their case remained secret as law enforcement continued to hunt for additional members of the FIN7 team.
Also appearing at the press conference were representatives from Visa and Master Card. Marie Russo, SVP of Cards and Franchise at MasterCard. Marie praised their participation in the NCFTA (the National Cyber Forensics Training Alliance) who offers a service that helps send stolen credit card information to the . Dan Schott, Senior Director of Visa. Both Ms. Russo and Mr. Schott talked about their proactive means of identifying crime trends and coordinated with banks. Mr. Schott reminded that every Visa card service in the United States offers "Transaction Alerts" that will notify you when your card is used in a transaction. (Unfortunately Schott also quoted the mythical $600 Billion annual cost of cybercrime.)
Is This Joker's Stash?
We don't know. Although many of the victim companies have been anonymized, the indictment does reveal that "Victim-1" was the Emerald Queen Hotel and Casino (EQC) in Pierce County, Washington, "Victim-3" was Chipotle Mexican Grill, Victim-5 was the Boeing Employee Credit Union, Victim-6 was Jason's Deli, Victim-8 was Red Robin Gourmet Burgers and Brews, Victim-9 was Sonic Drive-in, and Victim-10 was Taco John's. Trend Micro has previously published that FIN7 was also involved in breaches at Trump Hotels, Whole Foods, Saks Fifth Avenue and Lord & Taylor. That latter group of cards is known to have been trafficked on the criminal card market "Joker's Stash", and TrendMicro actually equates the groups. Their April 2, 2018 press release, "Bank Card Data of Five Million Stolen in Saks and Lord & Taylor Data Breach," begins with the sentence: "A hacking syndicate known as JokerStash (also identified as Fin7 and Carbanak) announced the sale of five million payment cards on the dark web last March 28.
 |
| Trend Micro (click for full article) |
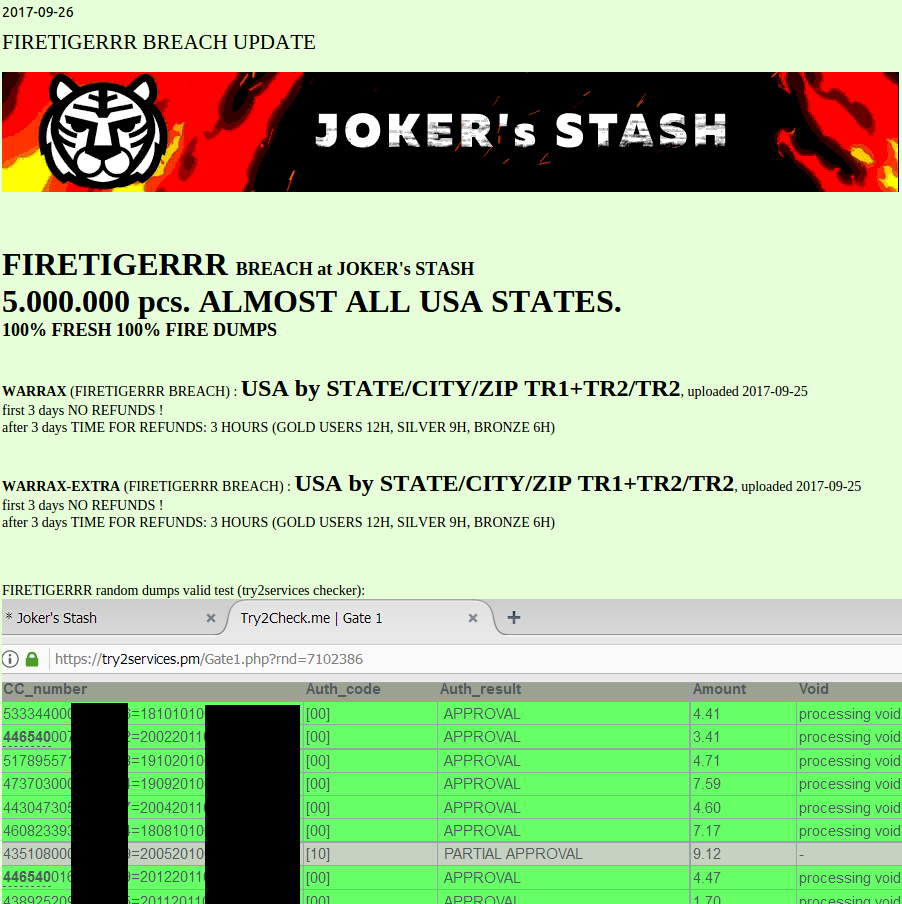 |
| Sonic Drive-In cards being sold on Joker's Stash (image from krebsonsecurity.com) |
The indictments do not make the ties between FIN7 and Joker's Stash quite so strongly. For example, in the Hladyr indictment:
(Related stories:
Fedor Gladyr, aka das, aka Fyodor, aka AronaXus, "served as a high-level systems administrator for FIN7 who maintained servers and communications channels used by the organization. For example, FIN7 members requested Gladyr grant them access to servers used by FIN7 to facilitate the malware scheme. He also played a management role in the scheme by delegating tasks and by providing instruction to other members of the scheme. Gladyr used Jabber and HipChat to communicate with his teams. The team used a JIRA server, usually used to track long software development projects, to communicate about the infiltration of their victims. As a few examples:
Google-translation of the ad:
Their "Contacts" page listed three addresses and telephone numbers:
"between approximately March 24, 2017 and April 18, 2017, FIN7 harvested payment data from point-of-sale devices at certain Victim-3 restaurant locations. FIN7 stole millions of payment card numbers, many of which have been offered for sale through vending sites, including but not limited to, Joker's Stash, thereby attempting to generate millions of dollars of illicit profits.
Three Ukrainian mastermind arrested
Three Ukrainians, Fedor Gladyr (age 33), Andrey Kolpakov (age 30), and Dmytro Fedorov (age 44) were arrested in the current round of actions, although prosecutors made it clear that there will be more arrests in the future. They also make clear that the top leader of this scheme has not yet been arrested.
Fedorov is said to have been the first to be arrested, in January 2018, in Poland. A KyivPost article in February about a 44-year old Ukrainian hacker being detained in Poland on an Interpol warrant is certainly about him ==> "Ukrainian Hacker detained, Faces 30 years in Prison."
It is unknown how or if this is related to the Spanish Police arrest of "Dennis-K" said at the time to be the leader of the Carbanak Group when he was arrested on March 26, 2018 in Alacante, Spain. (A YouTube video about that arrest (in Spanish) is available as "Detenido hacker 1000 millones (Denis-K)" The Times of London called Denis-K a 30-year old Russian-born Ukrainian citizen, living in Spain, whose malware used in cyber attacks in more than 40 countries, and who owned two million dollar houses. At the time, Europol said this was the end of a 5-year cybercrime spree that had stolen $1.2 Billion. This does NOT seem to be the same person, despite the age match and the "K" last name, as the US case states that Kolpakov was arrested in "late June" in Lepe, Spain.
It is also unknown how or if this is related to the Ukrainian Police's arrest of members of the COBALT game earlier this year. Europol says that COBALT and CARBANAK are the same group. It is believed by this author that the current FBI action in Seattle is targeting CUSTOMERS of the malware author group known as Cobalt/Carbanak. Hopefully this will get sorted out in the near future.
(Related stories:
"Mastermind behind 1 Billion Euro Cyber Bank Robbery Arrested in Spain" (Europol, March 26, 2018)
"Spain breaks up cybercrime gang after $1.2 billion spree" (AP, March 26, 2018) )
 |
| The superseding indictment of Fedor Gladyr |
07SEP2016 - Gladyr opens an "issue" for Victim-6 for his conspirators to upload files of internal credentials for the company network.
JAN2017 - Dmytro Fedorov opens an "issue" for Victim-7 credentials to be posted.
05APR2017 - Fedorov opens an "issue" for Victim-9 credentials to be posted.
Some of the malicious infiltration of the victim networks came by emailing those malware-laden requests for quotes to companies. Some examples include:
08AUG2016 - Victim-1, email from just_etravel@yahoo.com
08AUG2016 - Victim-1, email from frankjohnson@revital-travel.com
25AUG2016 - Victim-6, email from revital.travel@yahoo.com
21&23FEB2017 - Victim-2 two emails
24-25MAR2017 - Victim-3 six emails
05APR2017 - Victim-9 emails from oliver_palmer@yahoo.com
11APR2017 - Victim-4 email from oliver_palmer@yahoo.com
10MAR2017 - Victim-5 email
27MAR2017 - Victim-8 email from ray.donovan84@yahoo.com
25MAY2017 - Victim-4 email from Adrian.1987clark@yahoo.com (Subject: "takeout order")
12JUN2017 - Victim-10 email from Adrian.1987clark@yahoo.com (Attachment: order.catering.rtf)
In the case of Victim-1, firewall logs indicate that between August 8, 2016 and August 31, 2016, there were at least 3,639 communications between their organization and "revital-travel.com" addresses hosted on an IP address in Russia.
Not all of the emails were the "customer wanting a quote" type. On 21FEB2017, pen-testers working for the scheme sent emails purporting to be filings@sec.gov to Victim-2. The email contained a Microsoft Word attachment and alleged that an important filing was due and that the details for the filing were in the attached document.
Sometimes the stolen information targeted not only the business accounts, but also the personal information of the victims. One FIN7 member posted a Victim-2 employee's information to their JIRA server, showing screenshots from the employee's computer and including a text file with userids and passwords of their personal email account, LinkedIn account, and personal investment and banking accounts.
Once inside an organization, it was trivial for the FIN7 "pen-testers" to expand. Some documents posted in JIRA included userids and passwords for more than 1,000 employees, and in the case of Victim 3, point-of-sale malware was planted on many cash register computers nationwide, including 33 locations just in the Western District of Washington.
Victim-8 had an associated JIRA "issue" posted that included screenshots and usernames and passwords for the point-of-sale software management solution used by their restaurant chain. Hundreds of userids and passwords for employees in at least 798 different locations were also stolen from Victim-8 and posted in the JIRA server.
 |
| Kolpakov indictment |
Andrey Kolpakov, aka santisimo, aka sanisimoz, aka AndreyKS, participated in the scheme from at least September 2015 until June 20, 2018. In communications to and from Kolpakov, someone in the group referred to Fedir Hladyr and an individual still at large were the "main directors" of the group. That other individual was also called the "chief manager" of the team. Kolpakov was introduced to new recruits to the team as their supervisor. Kolpakov and Dmytro Fedorov had discussions about how to trigger the phishing emails, and which file types would be most effective. Kolpokov explained to Fedorov on 18SEP2017 that they now had a means to deploy a malware file without requiring the recipient to double-click on it. Kolpakov's account on the JIRA server was frequently the one that uploaded stolen data in response to the "issues" created by Gladyr. Many of the uploads mentioned in the Kolpakov indictment are about the particulars of exfiltrated files from password management systems, infrastructure management systems, and in one case an "employee only" web page that the team had altered to gather passwords. Team members regularly communicated on the JIRA server about recommendations for attack vectors to be used against targeted infrastructure.
 |
| Dmytro Fedorov Indictment |
Dmytro Fedorov's account on the JIRA server was involved in technical exploitation details. For example, in response to an "issue" created for Victim-7, Fedorov posted the results of data created by network mapping tools, including IP addresses and network, that helped to explain to the team what addresses should be targeted for further exploitation.
According to his indictment, Fedorov "served as a high-level pen-tester (one tasked with finding vulnerabilities that an attacker may exploit) who managed other pen-testers responsible for breaching the security of victims' computer systems. He specifically created and managed "issues" on the FIN7 JIRA server related to intrusions of multiple companies, including Victim-7 (an automotive retail and repair chain) and Victim-9 (Sonic Drive-Ins).
Fedorov's communications on Jabber seem to indicate that he was controlling the data exfiltration panels associated with malware planted on victim company computers and point-of-sale terminals.
Combi Security
Although the current indictments only name ten victim companies, the documentation presented by the US Attorney's office makes it clear that more than 100 companies were attacked by FIN7 hackers working for Combi Security.
 |
| FIN7 Attacked at least 3600 locations of 100+ US businesses |
If you wanted to have a team of the best hackers available, one option is recruiting people from the dark corners of the Internet, whose names and locations you may not know, and who may have been involved in every sort of trouble. The other option would be to stand up a cyber security company with offices in Moscow and Haifa, Israel, and advertise for the best trained White Hat hackers to come work for your Penetration Testing (Pen-Testing) team. FIN7 did the latter. Using hackers who applied in their real name, showed credentials and certifications, and were in some cases formerly the employees of their respective governments, Combi Security told their hackers that they had been hired to hack various companies, and then those hackers got to work penetrating systems.
Job ads found on a Ukrainian job board indicate that Combi Security had between 21-80 employees.
 |
| https://jobs.dou.ua/companies/combi-security/ |
Combi Security is one of the leading international companies in the field of information security. Its headquarters are located in Moscow and Haifa.
We are a team of leading professionals in the field of information security for various organizations working around the world.Our main specialization is a comprehensive audit of projects of any complexity, the supply of software and hardware.
Our main mission is to ensure the security of your activities, minimize the risks of using information technology. Every appeal to us for help is considered with the utmost thoroughness on an individual basis, offering an optimal solution within the framework of the tasks set and the specific needs expressed.
CombiSecurity.com offered their website in Russian, English, and Hebrew:
Their "Contacts" page listed three addresses and telephone numbers:
- Moscow , Presnenskaya naberezhnaya, 10, block C, tel. +7 (495) 3083827
- Haifa , 15-A Palyam St. (36 HaAtzmaut St) tel. +9 (724) 6328732
- Odessa , ul.Uspenskaya, 65 of office 23, 65011 phone. + 38 (048) 7002409
What services did they claim to provide? Below is their "The Services" page (Google-translated to English), retrieved from Archive.org's Wayback machine entry for CombiSecurity.com:
The services
A qualitatively working security service guarantees an indispensable stability in the operation of your technologies.
Thanks to the active assistance of our technical experts, all the irregularities in the operation of your devices will certainly be detected, analyzed and eliminated. With our professional support, the disrupted monitoring of the security system will turn into a stable process, managed in accordance with established principles and rules.
We provide services:
Penetration test (Pentest)
- Technological penetration test.This penetration test is conducted to identify existing vulnerabilities in the elements of the IT infrastructure, practical demonstration of the possibility of using vulnerabilities (by the example of the most critical ones) and the formation of recommendations for the removal of identified vulnerabilities.A penetration test can be conducted for the perimeter of the corporate network (external test) and for internal resources (internal test). Work can be conducted with notification to administrators and users of the system under test, or without it. During internal testing, both the auditor's laptop and the customer's standard workplace can be used.In the testing process, both tools and manual analysis methods are used.
- Socio-technical penetration test.This penetration test is conducted using social engineering techniques. The main purpose of the test is to identify the level of awareness of the Customer's personnel about the requirements for information security. In the process of testing, the response of users and personnel responsible for information security to the organizational methods of penetration used by attackers is determined.Methods of social engineering are often used by intruders and are directed, as a rule, to end users. As a result of a successful attack, an attacker can gain control over workstations, obtain confidential Customer documents, use the Customer's resources to organize attacks on the systems of other companies, send out spam, etc.The organizational aspects of information security are an important part of the protection system and, often, ordinary users are the weakest link. The given service will allow to reveal those organizational aspects of information security, on which the Customer should pay attention first of all.The results obtained during the provision of this service can form the basis for the development of the Security Awareness Program, which is maximally focused on the problem areas identified during the testing. This service can also be useful for checking the effectiveness of the current Customer Awareness Program.
- Integrated penetration test.Complex penetration test is closest to the real actions of intruders. Using various technical and socio-engineering methods, auditors try to bypass existing protective mechanisms in order to fulfill the tasks set by the Customer (increasing privileges, gaining access to confidential information, modifying data from DBMS, etc.).During testing, the approaches described in the sections "Technological penetration test" and "Sociotechnical penetration test" are used, and the security of the customer's wireless networks is assessed.
The result of the work will be a report containing :
- Methods of testing.
- Conclusions for management, containing an overall assessment of the level of security.
- Description of the identified deficiencies of the ISMS.
- Description of the testing process with information on all identified vulnerabilities and the results of their operation.
- Recommendations for the elimination of identified vulnerabilities.
Controlling the level of security
Due to the rapid detection of vulnerabilities and the introduction of changes to the network infrastructure, the results of a one-time verification of the level of security of the corporate network quickly lose their relevance. The need for new inspections arises after several months, and in companies with a dynamically developing IT infrastructure and a large-scale representation on the Internet, this period can be weeks or even days.
The emergence of new vulnerabilities, the change in the structure of the network perimeter, the modification of the settings of servers, network equipment and security equipment, all this requires in-depth analysis on the effect on the resistance to external unauthorized influences.
In this regard, Combi Security Company offers to your attention services aimed at constant monitoring of the state of information security. These include:
- Monitoring the perimeter security of the corporate network
- Designing and implementing a security management system
- Development of corporate security policy
Evaluation of the level of security
Penetration testing works are aimed at overcoming existing protective mechanisms, but not at a deep assessment of the level of security of a specific information system or technology. The penetration approach of the black box analysis often prevents the auditor from detecting some vulnerabilities that are easily detected by other methods, for example, by analyzing firewall settings.
The work to assess the level of security is aimed at a deep assessment of one or another aspect of information security, or a comprehensive analysis of the entire ISMS in general.
Combi Security offers the following services to assess the level of security of various aspects of information security:
- Integrated audit of information security
- Assessing the security of Web applications
- Analysis of application security on mobile platforms
- Assessing the security of wireless networks
- The effectiveness of the awareness-raising program in the field of information security
Raising awareness of users
Preparing for audit in accordance with international standards, for example ISO 27001
Consultations of experts in the field of it- security.
In addition to these services, sometimes there is a need for solving non-standard tasks. If you did not find something that will help you solve the problem before you, you can contact the experts of Combi Security. Perhaps our specialists have already dealt with similar problems.
Our company offers only those services that we can really carry out with very high quality, services where we can fully utilize the rich practical experience of our specialists.




No comments:
Post a Comment
Trying a new setting. After turning on comments, I got about 20-30 comments per day that were all link spam. Sorry to require login, but the spam was too much.