What’s in the Name: Call it IcedID or TrickBot? Tell that to a security researcher (Arsh Arora in this case) and watch them RANT
(Gar-note: today's blog post is a guest blog from malware analyst, Arsh Arora...)
Today’s
post starts with an interesting link from Dawid Golak's Medium post: “IcedID aka# Bokbot Analysis with Ghidra” which mentions that IcedID is dropping TrickBot. Although the article is about IcedID, it gets confusing quickly, because the researcher focused on finding artifacts for IcedID instead finds TrickBot artifacts. A big
question for the security industry still remain is to how to classify the
malware from the originator or the binary that is being dropped. We followed up on the sample he mentioned and saw the same thing. This is definitely Trickbot.
First Stage – Sample Collection from Virus Total Intelligence
In the "AnyRun Analysis" linked to by Dawid, the TrickBot
binary was downloaded from “54.36.218[.]96
(slash) tin[.]exe
Virus
total link (50/ 71 detections) https://www.virustotal.com/intelligence/search/?query=84878B4967A4243CD904794F3B8B2812
 |
| Fig 1: TrickBot Sample |
Second Stage – Sample Execution
After
the execution in a virtual environment, I was able to see TrickBot behavior
similar to what we have documented in the past in our post "Trickbot's New Magic Trick: Sending Spam":
A large number
of config files and dlls were loaded into the Roaming/netcache/Data, a unique behavior of the TrickBot binary.
 |
| Fig 2: Configs and Dlls Loaded |
Third Stage – Open Firefox and visit different Bank website
It
is often the case that to get any banking trojan to co-operate with the
researcher, some initiation from the researcher side is needed. Due to past
experience, I have learned that one needs to open up a browser and visit
different bank websites to activate the banking trojan. The trojan resists
until instigated by visits to these pages. I visited close to 20 different bank
websites and was able to obtain injects from 7 of those bank websites. The injects and admin login panels of the
websites are as follows.
Name of
Bank
|
Admin Login Panel
|
IP
|
Location
|
Bank of
America
|
https://aefaldnessliverhearted[.]com/load/
|
185.242.6.245
|
AS9009, Prague
|
Chase
|
https://aefaldnessliverhearted[.]com/load/
|
185.242.6.245
|
AS9009, Prague
|
Citi
|
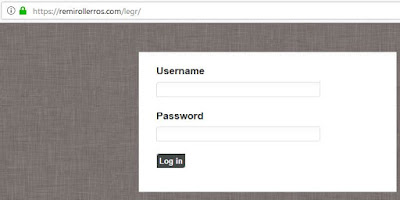
https://remirollerros[.]com/legr/
|
109.234.37.246
|
AS48282, RU
|
Usaa
|
https://onlylocaltrade[.]com/lob.php
|
185.87.187.198
|
AS48635,NL
|
WellsFargo
|
https://wellsfargostrade.com/2wells2
|
185.36.189.143
|
AS50673, NL
|
PNC
|
https://wellsfargostrade[.]com/pncadmin/index.php
|
185.36.189.143
|
AS50673, NL
|
53 Bank
|
https://wellsfargostrade[.]com/53repadmin2
|
185.36.189.143
|
AS50673, NL
|
When infected, viewing the source code while visiting one of the banks is all that is needed to identify the data exfiltration destination. Some examples follow from this infection run:
BankofAmerica
 |
| Fig 3: BoA Web Inject |
Chase
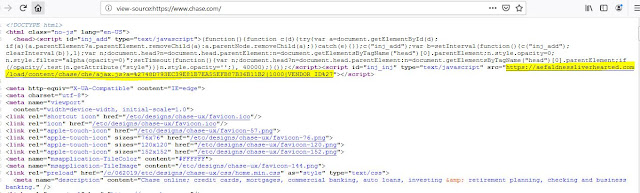 |
| Fig 4: Chase Web Inject |
 |
| Fig 5: BoA and Chase Admin Panel |
Citi
 |
| Fig 6: Citi Web Inject |
USAA
 |
| Fig 8: USAA Web Inject |
WellsFargo
 |
| Fig 9: WellsFargo Web Inject |
 |
| Fig 10: WellsFargo Admin Panel |
PNC
 |
| Fig 11: PNC Web Inject |
 |
| Fig 12: PNC Admin Panel |
53 Bank
 |
| Fig 13: 53 Bank Web Inject |
 |
| Fig 14: 53 Bank Admin Panel |
For more details please contact Arsh Arora (ararora at uab.edu) or Gary Warner (gar at uab.edu) at UAB. Please note: Arsh is defending his PhD this summer and looking for new opportunities.