Maulvi Ameer Khan Muttaqi - Foreign Minister
TAi.026 Name: 1: AMIR KHAN 2: MOTAQI 3: na 4: na
Name (original script): امیر خان متقی
Title: Mullah
Designation: a) Minister of Education under the Taliban regime
b) Taliban representative in UN-led talks under the Taliban regime
DOB: Approximately 1968
POB: a) Zurmat District, Paktia Province, Afghanistan
b) Shin Kalai village, Nad-e-Ali District, Helmand Province, Afghanistan
Good quality a.k.a.: Amir Khan Muttaqi
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: na
Listed on: 25 Jan. 2001 ( amended on
3 Sep. 2003, 21 Sep. 2007, 29 Nov. 2011 )
Other information: Member of the Taliban Supreme Council as at June 2007. Believed to be in Afghanistan/Pakistan border area. Belongs to Sulaimankhel tribe. Review pursuant to Security Council resolution 1822 (2008) was concluded on 21 Jul. 2010.
Mullah Hidayatullah Badri (Gul Agha) - Finance Minister
TAi.147 Name: 1: GUL 2: AGHA 3: ISHAKZAI 4: na
Name (original script): كُل آغا اسحاقزی
Title: na
Designation: na
DOB: Approximately 1972
POB: Band-e Temur, Maiwand District, Kandahar Province, Afghanistan
Good quality a.k.a.: a) Mullah Gul Agha
b) Mullah Gul Agha Akhund
Low quality a.k.a.: a) Hidayatullah
b) Haji Hidayatullah
c) Hayadatullah
Nationality: na
Passport no: na
National identification no: na
Address: Pakistan
Listed on: 20 Jul. 2010 ( amended on
29 Nov. 2011, 31 Dec. 2013 )
Other information: Member of a Taliban Council that coordinates the collection of zakat (Islamic tax) from Baluchistan Province, Pakistan. Head of Taliban Financial Commission as at mid-2013. Associated with Mullah Mohammed Omar (TAi.004). Served as Omar's principal finance officer and one of his closest advisors. Belongs to Ishaqzai tribe.
Sheikh Maulvi Noorullah Munir - Education Minister
(no apparent UN sanctions - please provide more information in comments below!)
Mullah Khairullah Khairkhwa - Minister Information and Culture
TAi.093 Name: 1: KHAIRULLAH 2: KHAIRKHWAH 3: na 4: na
Name (original script): خيرالله خيرخواه
Title: a) Maulavi
b) Mullah
Designation: a) Governor of Herat Province under the Taliban regime
b) Spokesperson of the Taliban regime
c) Governor of Kabul province under the Taliban regime
d) Minister of Internal Affairs under the Taliban regime
DOB: Approximately 1963
POB: Poti village, Arghistan district, Kandahar province, Afghanistan
Good quality a.k.a.: a) Mullah Khairullah Khairkhwah
b) Khirullah Said Wali Khairkhwa, born in Kandahar on 01 Jan.1967
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: Qatar
Listed on: 25 Jan. 2001 ( amended on
3 Sep. 2003, 21 Sep. 2007, 3 Oct. 2008, 12 Apr. 2010, 29 Nov. 2011, 31 Dec. 2013, 7 Sep. 2016 )
Other information: Belongs to Popalzai tribe. Review pursuant to Security Council resolution 1822 (2008) was concluded on 23 Jul. 2010.
Qari Din Hanif - Minister of Economy
TAi.043 Name: 1: DIN MOHAMMAD 2: HANIF 3: na 4: na
Name (original script): دین محمد حنیف
Title: Qari Designation: a) Minister of Planning under the Taliban regime b) Minister of Higher Education under the Taliban regime DOB: Approximately 1955 POB: Shakarlab village, Yaftali Pain District, Badakhshan Province, Afghanistan Good quality a.k.a.: a) Qari Din Mohammad b) Iadena Mohammad born 1 Jan. 1969 in Badakhshan Low quality a.k.a.: na Nationality: Afghanistan Passport no: OA 454044, issued in Afghanistan National identification no: na Address: na Listed on: 25 Jan. 2001 ( amended on 3 Sep. 2003, 9 Jul. 2007, 21 Sep. 2007, 29 Nov. 2011, 25 Oct. 2012, 7 Sep. 2016 ) Other information: Member of Taliban Supreme Council responsible for Takhar and Badakhshan provinces. Believed to be in Afghanistan/Pakistan border area. Review pursuant to Security Council resolution 1822 (2008) was concluded on 27 Jul. 2010.
Sheikh Maulvi Noor Muhammad Saqib - Minister Hajj and Religious Affairs
TAi.110 Name: 1: NOOR MOHAMMAD 2: SAQIB 3: na 4: na
Name (original script): نور محمد ثاقب
Title: na
Designation: Chief Justice of Supreme Court under the Taliban regime
DOB: Approximately 1958
POB: a) Bagrami District, Kabul Province, Afghanistan
b) Tarakhel area, Deh Sabz District, Kabul Province, Afghanistan
Good quality a.k.a.: na
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: na
Listed on: 25 Jan. 2001 ( amended on
3 Sep. 2003, 21 Sep. 2007, 29 Nov. 2011 )
Other information: Member of Taliban Supreme Council and Head of Taliban Religious Committee. Belongs to Ahmadzai tribe. Review pursuant to Security Council resolution 1822 (2008) was concluded on 23 Jul. 2010.
Maulvi Abdul Hakim Sharia - Minister of Justice
(no apparent UN sanctions under TAi - please provide more information in comments below!)
possibly QDi.120
Mullah Noorullah Noori - Minister for Borders and Tribal Affairs
TAi.089 Name: 1: NURULLAH 2: NURI 3: na 4: na
Name (original script): نور الله نوری
Title: Maulavi
Designation: a) Governor of Balkh Province under the Taliban Regime
b) Head of Northern Zone under the Taliban regime
DOB: a) Approximately 1958
b) 1 Jan. 1967
POB: Shahjoe District, Zabul Province, Afghanistan
Good quality a.k.a.: Norullah Noori
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: Qatar
Listed on: 25 Jan. 2001 ( amended on
3 Sep. 2003, 21 Sep. 2007, 29 Nov. 2011, 31 Dec. 2013, 7 Sep. 2016 )
Other information: Belongs to Tokhi tribe. Review pursuant to Security Council resolution 1822 (2008) was concluded on 29 Jul. 2010.
Mullah Muhammad Younas Akhundzada - Minister for Rural Rehabilitation and Development
(no apparent UN sanctions - please provide more information in comments below!)
Sheikh Muhammad Khalid - Minister for Dawat & Irshaad (Preaching and Guidance) and Amr Bil Maroof Wa Anil Munkar
(no apparent UN sanctions - please provide more information in comments below!)
Mullah Abdul Mannan Omari - Minister for Public Works
(no apparent UN sanctions - please provide more information in comments below!)
Mullah Muhamad Essa Akhund - Minister for Mines and Petroleum
TAi.060 Name: 1: MOHAMMAD ESSA 2: AKHUND 3: na 4: na
Name (original script): محمد عیسی آخوند
Title: a) Alhaj
b) Mullah
Designation: Minister of Water, Sanitation and Electricity under the Taliban regime
DOB: Approximately 1958
POB: Mial area, Spin Boldak District, Kandahar Province, Afghanistan
Good quality a.k.a.: na
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: na
Listed on: 25 Jan. 2001 ( amended on
3 Sep. 2003, 21 Sep. 2007, 29 Nov. 2011 )
Other information: Belongs to Nurzai tribe. Review pursuant to Security Council resolution 1822 (2008) was concluded on 27 Jul. 2010.
Mullah Abdul Latif Mansoor - Minister for Water and Power
TAi.007 Name: 1: ABDUL LATIF 2: MANSUR 3: na 4: na
Name (original script): عبد اللطيف منصور
Title: Maulavi
Designation: Minister of Agriculture under the Taliban regime
DOB: Approximately 1968
POB: a) Zurmat District, Paktia Province, Afghanistan
b) Garda Saray District, Paktia Province, Afghanistan
Good quality a.k.a.: a) Abdul Latif Mansoor
b) Wali Mohammad
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: na
Listed on: 31 Jan. 2001 ( amended on
3 Sep. 2003, 18 Jul. 2007, 21 Sep. 2007, 13 Feb. 2012, 18 May 2012, 22 Apr. 2013 )
Other information: Taliban Shadow Governor for Logar Province as of late 2012. Believed to be in Afghanistan/Pakistan border area. Belongs to Sahak tribe (Ghilzai). Review pursuant to Security Council resolution 1822 (2008) was concluded on 27 Jul. 2010. I
Hameedullah Akhundzada - Minister for Civil Aviation & Transport
(no apparent UN sanctions - please provide more information in comments below!)
Abdul Baqi Haqqani - Minister for Higher Education
Not a positive match ==> possibly TAi.038 Please comment if you can clarify!
TAi.038 Name: 1: ABDUL BAQI 2: BASIR 3: AWAL SHAH 4: na
Name (original script): عبد الباقي بصير أول شاه
Title: a) Maulavi
b) Mullah
Designation: a) Governor of Khost and Paktika provinces under the Taliban regime
b) Vice-Minister of Information and Culture under the Taliban regime
c) Consular Department, Ministry of Foreign Affairs under the Taliban regime
DOB: Between 1960 and 1962 (Approximately )
POB: a) Jalalabad City, Nangarhar Province, Afghanistan
b) Shinwar District, Nangarhar Province, Afghanistan
Good quality a.k.a.: Abdul Baqi (previously listed as)
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: na
Listed on: 23 Feb. 2001 ( amended on
3 Sep. 2003, 7 Sep. 2007, 21 Sep. 2007, 29 Nov. 2011, 13 Aug. 2012 )
Other information: Believed to be in Afghanistan/Pakistan border area. Taliban member responsible for Nangarhar Province as at 2008. Until 7 Sep. 2007 he was also listed under number TAi.048. Review pursuant to Security Council resolution 1822 (2008) was concluded on 1 Jun. 2010.
Najibullah Haqqani - Minister for Communications
Ai.071 Name: 1: NAJIBULLAH 2: HAQQANI 3: HIDAYATULLAH 4: na
Name (original script): نجیب الله حقانی هدايت الله
Title: Maulavi
Designation: Deputy Minister of Finance under the Taliban regime
DOB: 1971
POB: Moni village, Shigal District, Kunar Province
Good quality a.k.a.: Najibullah Haqani
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: Afghan national identification card (tazkira) number 545167 (issued in 1974)
Address: na
Listed on: 23 Feb. 2001 ( amended on
3 Sep. 2003, 18 Jul. 2007, 21 Sep. 2007, 27 Sep. 2007, 29 Nov. 2011, 16 May 2014 )
Other information: Cousin of Moulavi Noor Jalal. Grandfather’s name is Salam. Taliban member responsible for Laghman Province as of late 2010. Believed to be in Afghanistan/Pakistan border area. Review pursuant to Security Council resolution 1822 (2008) was concluded on 1 Jun. 2010.
Khalil ur Rehman Haqqani - Minister for Refugees
TAi.150 Name: 1: KHALIL 2: AHMED 3: HAQQANI 4: na
Name (original script): خلیل احمد حقانی
Title: Haji
Designation: na
DOB: a) 1 Jan. 1966
b) Between 1958 and 1964
POB: Sarana Village, Garda Saray area, Waza Zadran District, Paktia Province, Afghanistan
Good quality a.k.a.: a) Khalil Al-Rahman Haqqani
b) Khalil ur Rahman Haqqani
c) Khaleel Haqqani
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: a) Peshawar, Pakistan
b) Near Dergey Manday Madrasa in Dergey Manday Village, near Miram Shah, North Waziristan Agency (NWA), Federally Administered Tribal Areas (FATA), Pakistan
c) Kayla Village, near Miram Shah, North Waziristan Agency (NWA), Federally Administered Tribal Areas (FATA), Pakistan
d) Sarana Zadran Village, Paktia Province, Afghanistan
Listed on: 9 Feb. 2011 ( amended on
1 Jun. 2012 )
Other information: Senior member of the Haqqani Network (TAe.012), which operates out of North Waziristan in the Federally Administered Tribal Areas of Pakistan. Has previously traveled to, and raised funds in, Dubai, United Arab Emirates. Brother of Jalaluddin Haqqani (TAi.040) and uncle of Sirajuddin Jallaloudine Haqqani (TAi.144).
Mullah Abdul Haq Wasiq - Director General of Intelligence
TAi.082 Name: 1: ABDUL-HAQ 2: WASSIQ 3: na 4: na
Name (original script): عبد الحق وثيق
Title: Maulavi
Designation: Deputy Minister of Security (Intelligence) under the Taliban regime
DOB: a) 1971
b) Approximately 1975
POB: Gharib village, Khogyani District, Ghazni Province, Afghanistan
Good quality a.k.a.: a) Abdul-Haq Wasseq
b) Abdul Haq Wasiq
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: Qatar
Listed on: 31 Jan. 2001 ( amended on
3 Sep. 2003, 21 Sep. 2007, 3 Oct. 2008, 29 Nov. 2011, 31 Dec. 2013, 11 Feb. 2014, 7 Sep. 2016 )
Other information: Review pursuant to Security Council resolution 1822 (2008) was concluded on 27 Jul. 2010.
Haji Muhammad Idris - Director General of Afghanistan Bank
(no apparent UN sanctions - please provide more information in comments below!)
Maulvi Ahmed Jan Ahmadi - Director General of Administrative Affairs
Possibly TAi.159 - but unclear. If you can help clarify, please comment below
TAi.159 Name: 1: AHMED JAN 2: WAZIR 3: AKHTAR MOHAMMAD 4: na
Name (original script): احمد جان وزیر اختر محمد
Title: na
Designation: Official of the Ministry of Finance during the Taliban regime
DOB: 1963
POB: Barlach Village, Qareh Bagh District, Ghazni Province, Afghanistan
Good quality a.k.a.: a) Ahmed Jan Kuchi
b) Ahmed Jan Zadran
Low quality a.k.a.: na
Nationality: na
Passport no: na
National identification no: na
Address: na
Listed on: 6 Jan. 2012 ( amended on
31 Dec. 2013, 11 Feb. 2014 )
Other information: Key commander of the Haqqani Network (TAe.012), which is based in Afghanistan/Pakistan border area. Acts as deputy, spokesperson and advisor for Haqqani Network senior leader Sirajuddin Jallaloudine Haqqani (TAi.144). Liaises with the Taliban Supreme Council. Has travelled abroad. Liaises with and provides Taliban commanders in Ghazni Province, Afghanistan, with money, weapons, communications equipment and supplies. Reportedly deceased as of 2013.
Mullah Muhammad Fazil Mazloom Akhund - Deputy to Defense Minister
TAi.023 Name: 1: FAZL MOHAMMAD 2: MAZLOOM 3: na 4: na
Name (original script): فضل محمد مظلوم
Title: Mullah
Designation: Deputy Chief of Army Staff of the Taliban regime
DOB: Between 1963 and 1968
POB: Uruzgan, Afghanistan
Good quality a.k.a.: a) Molah Fazl
b) Fazel Mohammad Mazloom
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: na
National identification no: na
Address: Qatar
Listed on: 23 Feb. 2001 ( amended on
3 Sep. 2003, 21 Sep. 2007, 3 Oct. 2008, 31 Dec. 2013, 7 Sep. 2016 )
Other information: Review pursuant to Security Council resolution 1822 (2008) was concluded on 23 Jul. 2010.
Qari Fasihuddin (Tajik) - Chief of Army
(said to be killed by airstrike according to the Afghanistan Ministry of Defense)
Sher Muhammad Abbas Stanakzai - Deputy Foreign Minister
https://en.wikipedia.org/wiki/Sher_Mohammad_Abbas_Stanikzai
Maulvi Noor Jalal - Deputy Interior Minister
(no apparent UN sanctions - please provide more information in comments below!)
Zabihullah Mujahid - Deputy Minister of Information and Broadcasting
(no apparent UN sanctions - please provide more information in comments below!)
Mullah Taj Mir Jawad - 1st Deputy to Intelligence Chief (H)
(no apparent UN sanctions - please provide more information in comments below!)
Mullah Rahmatullah Najib - Administrative Depty to Intelligence Chief
possibly TAi.137 - if you can clarify, please comment below!
TAi.137 Name: 1: RAHMATULLAH 2: KAKAZADA 3: na 4: na
Name (original script): رحمت الله کاکا زاده
Title: a) Maulavi
b) Mullah
Designation: Consul General, Taliban Consulate General,
Karachi, Pakistan
DOB: 1968
POB: Zurmat District, Paktia Province, Afghanistan
Good quality a.k.a.: a) Rehmatullah
b) Kakazada
Low quality a.k.a.: Mullah Nasir
Nationality: Afghanistan
Passport no: D 000952, issued on
7 Jan. 1999, issued in Afghanistan
National identification no: na
Address: na
Listed on: 25 Jan. 2001 ( amended on
3 Sep. 2003, 25 Jul. 2006, 18 Jul. 2007, 21 Sep. 2007, 29 Nov. 2011 )
Other information: Taliban member responsible for Ghazni Province, Afghanistan, as of May 2007. Head of an intelligence network. Believed to be in Afghanistan/Pakistan border area. Belongs to Suleimankheil tribe. Review pursuant to Security Council resolution 1822 (2008) was concluded on 21 Jul. 2010.
Mullah Abdul Haq Akhund - Deputy Minister of Interior for Counter Narcotics Affairs
possibly TAi.051 - if you can clarify,please comment below!
TAi.051 Name: 1: ABDULHAI 2: MOTMAEN 3: na 4: na
Name (original script): عبدالحی مطمئن
Title: Maulavi
Designation: a) Director of the Information and Culture Department in Kandahar Province under the Taliban regime
b) Spokesperson of the Taliban regime
DOB: Approximately 1973
POB: a) Shinkalai village, Nad-e-Ali District, Helmand Province, Afghanistan
b) Zabul Province, Afghanistan
Good quality a.k.a.: Abdul Haq son of M. Anwar Khan (عبد الحق ولد محمد انور خان) (Afghan passport number OA462456, issued on 31 Jan. 2012 (11-11-1390) by the Afghan Consulate General in Peshawar, Pakistan)
Low quality a.k.a.: na
Nationality: Afghanistan
Passport no: Afghanistan number OA462456, issued on
31 Jan. 2012 (issued under the name of Abdul Haq)
National identification no: na
Address: na
Listed on: 23 Feb. 2001 ( amended on
3 Sep. 2003, 21 Sep. 2007, 29 Nov. 2011, 31 Dec. 2013, 16 May 2014 )
Other information: Family is originally from Zabul, but settled later in Helmand. Member of the Taliban Supreme Council and spokesperson for Mullah Mohammed Omar (TAi.004) as of 2007. Believed to be in Afghanistan/Pakistan border area. Belongs to Kharoti tribe. Review pursuant to Security Council resolution 1822 (2008) was concluded on 23 Jul. 2010.
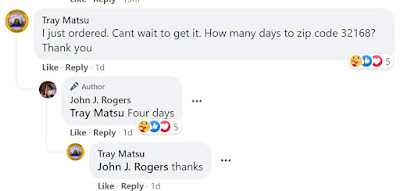
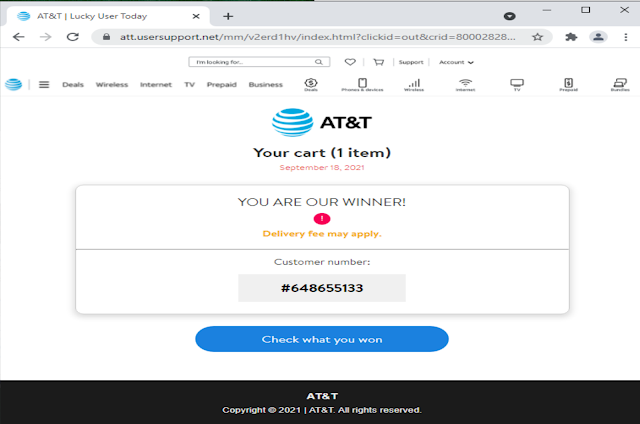
 That's the ad they saw on Facebook. "Due to special reasons" the company has decided to "sell the last batch of laptops." If you click the Shop Now button, it takes you to the website "maxwellplaceonhudson[.]com"
That's the ad they saw on Facebook. "Due to special reasons" the company has decided to "sell the last batch of laptops." If you click the Shop Now button, it takes you to the website "maxwellplaceonhudson[.]com"