If you live in the United States and have an AT&T phone, you are almost certainly receiving SMS messages that look something like this:
AT&T Free Msg: August bill is paid. Thanks, MARY! Here's a little gift for you: n9cxr[.]info/dhmxmcmBTQ (from +1 (718) 710-0863)
or
AT&T Free Msg: August bill processed. Thanks, Mary! Here's a little something for you: l4bsn[.]info/C2Lx3oggFi (from +1 (332) 220-7291)
or
AT&T Free Msg: Latest bill is paid. Thanks, Fedencia! Here's a little freebie for you: k5amw[.]info/VloTBdytEl (from +1 (870) 663-5472)
AT&T has sort of trained us that it's cool to get messages from them with links in them. Every time your bill is available, or paid, or has a new charge, you get a text message from them that starts with "AT&T Free Msg:" and ends with a link such as "att.com/myattapp" or "att.com/myViewBill."
This is where some independent amateur researchers make a mistake. If you visit the URL in the first message from your Windows computer, you are automagically forwarded to Google.
"Never heard of it - why don't you go to Google instead." by sending a "302 redirect."
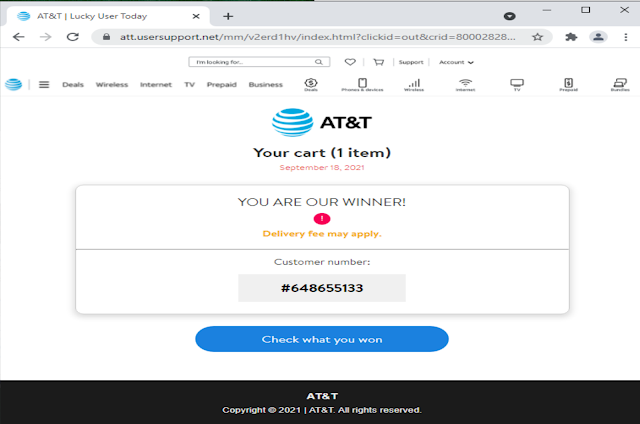
Once I change my Chrome Virtual Machine to pretend to be "Safari on iPhone" we revisit the URL that was sent to my phone:
We've written several times in the past about these never-ending surveys. Their objective is to gather as much personal data from you as they can and to show you as many advertisements as they can. They then experience revenue by both showing you ads during the survey, but also by selling the personal information that they gather you to organizations that need "qualified sales leads." They will tell those organizations that you are looking for things like savings on college tuition, health insurance, car insurance, electronics, a new vehicle, etc, and you will start getting more spam messages from those organizations who will have believed that you asked for their spam!
We asked our friends at Zetalytics, via their Zone Cruncher tool, "So where in the world is the IP address n9cxr[.]info?" They told us that it is located in Hong Kong on a server that is hosted by Alibaba Inc.
All of those domains are of course registered at the scummy domain registrar NameCheap. They claim that if we inform them of bad domains, they will de-register them. Once I post this, I'll send them a copy and report back what happens.
By the way, the content is not exactly the same with each visit. My next visit to the n9cxr URL gave me this pop-up instead:
So how are we getting to the fake AT&T page? That's where a tool that CAUCE Director Neil Schwartman showed me comes in. While I don't recommend the company necessarily, this little Chrome plug-in is gold for mapping out redirect paths! (Search for the Chrome Extension "Ayima Redirect Path" and please remember you should only be reviewing potentially hostile URLs in a Virtual Machine!)What does all that mean? It tells us that the first URL's webserver claimed that the page we were looking for "dhmxmcmBTQ" had been temporarily redirected to "themechallenge[.]club" and that we should ask that server for a particular "key."
redirect.usersupport[.]net => hosted on 2606:4700:3032::6815:2b25
By the way, do you remember the "key" we had to pass? In a similar way to our User-Agent, if you visit one of these sites and fail to pass it a "key" it will just redirect you to 127.0.0.1, which means, "visit your own machine."
Not just AT&T!
List of SMS-spam-abusing .info (and .xyz) domains believed to be associated with these campaigns. It sort of makes sense that there are exactly 100 of them.














Thanks for the information! Been getting texts from random numbers saying all those things. So annoying!!
ReplyDeleteNCREDIBLY INFORMATIVE. Thank you for sharing your hard work!
ReplyDeleteDon't know how to attach screen shot, but received this 8 hours ago in text. When hit link (stupid I know, I never do. This is a first) opened in my Opera browser in desktop mode & kicked to Google search.
From: +1 773-610-8033
Text was:
AT&T Free Msg: August bill is paid. Thanks, CAROL! Here's a little freebie for you: v4mxv.info/ZO1pDJAsQF
Thanks for the info! I get these daily.
ReplyDeleteFrom: +1 (915) 808-2870
AT&T Free Msg: Latest bill is paid. Thanks! Here's a little freebie for you: v7msz.info/1mLwJUCD3a
Verizon Free Msg: August bill is paid. Thanks, Dave! Here's a little something for you: z7emb.info/WnITbkbtes
ReplyDelete