Arsh take it from here.
Amazon Gift Card from Kelihos botnet! Anyone up for a Nymaim banking trojan or CryptoLocker?
Here it is, the Kelihos botnet back with a bang. Today, Kelihos is in a festive mood and giving away a free “Amazon Gift Card”, especially for US customers. Instead of ALL American spam recipients receiving the malware, however, only those whose email ends in the country code ".us" received this malware. As you can see in the sample list below, this means that many school employees will have received this spam, as K-12 schools very commonly use .us domain names.This is the first time it has geo-targeted US customers, unlike previous occasions where it had targeted Canadian [Canada] , German and UK, [German and UK] and Dutch [Dutch] customers. The delivery mechanism is the same in which the botnet delivers emails containing suspicious links to a Microsoft Word document that will download a Nullsoft installer and eventually affect you with Nymaim/CryptoLocker.
Now, we can surely say that the operators of Kelihos botnet are formulating a strategy in choosing their targets for the spam campaign. Basically, they are trying to gain back the attention of the industry and trying to proclaim its spot of the longest surviving spamming botnet. Recently, the botnet size increased tremendously and has been a hot topic among the cyber industry.
 |
| Geo Targeted emails to US based victims |
The body of the message sent contains a malicious word doc link
Subject: Amazon Gift Team just wants to make a present for you
Hi our beloved client!
Our company glad to notify, that our improbable promotion special offer to say thanks to limited number of our buyers.
In this greetings list you can find costless Amazon Gift Card for $65 balance!!! It can be redeemed in our online webstore for any further purchase on Amazon. You can activate promo eGift using this link: hxxp://amazon[.]com[.]yougifted[.]pw/Amazon%20Gift%20Code[dot]doc
Hurry up! This offer have limited time, and limited number of promo vouchers available, that can be activated during promo, so do not forget to obtain your one!
Huge thanks from Amazon for being a part of our team, we really apreciate that!
----------------------------------------
You can discover useful information using our FAQ on amazon.com/contact-us or via the phone +180012343212
Amazon Promo Team
______________________________________________
Subject: Amazon Gift Team just wants to make a present for you
Subject: Awesome news! You recieved a gift from Amazon!
Subject: Don't wait, get free voucher! Amazon Promo chosen you!
Subject: Gift from Amazon was just recieved, redeem yours now
The URLs sent in the email are presented below with its corresponding resolved IP address, via WHOIS search
hxxp://amazon.com.yougifted[.]pw/Amazon%20Gift%20Code[dot]doc – 104[.]168[.]181[.]99; Oklahoma
hxxp://amazon.com.youwelcomes[.]pw/Amazon%20Gift%20Code[dot]doc – 104[.]168[.]181[.]99
hxxp://amazon.com.cheappromo[.]pw/Amazon%20Gift%20Code[dot]doc – 149[.]202[.]194[.]178; Nord-pas-de-calais
hxxp://amazon.com.getforless[.]pw/Amazon%20Gift%20Code[dot]doc - 149[.]202[.]194[.]178
hxxp://amazon.com.giftcardservice[.]pw/Amazon%20Gift%20Code[dot]doc – 198[.]105[.]215[.]36; Utah
An interesting observation is that 4 out of 5 Urls share the same Whois contact information[Whois]
Registrant Name: Frank Gilmer
Registrant Organization: Private Person
Registrant Street: 22 Bakinskih komissarov 2k1, 51
Registrant City: Moscow
Registrant State/Province: Moscow
Registrant Postal Code: 119571
Registrant Country: RU
Registrant Phone: +7.9681673922
Registrant Email: frankgilmer416@gmail.com
Moving on, the delivery mechanism remains to consistent as seen on previous occasions
 |
| Document opened in Protected view with a URL link |
 |
| Enable Content AKA Encrypt Me! |
 |
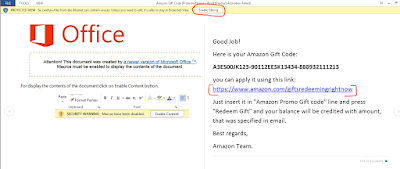
| Congratulating the user! |
This behavior has been seen for the first time where the user is asked to click a URL. While the user is occupied trying to find his/her gift code, the ransomware is performing its task in the background. By the time the user realizes a scam is underway, the machine is already encrypted. Threat actors have perfectly social engineered user behavior in order to succeed in causing damage to the user.
The URL provided in the email doesn't actually exist at Amazon:
hxxps://www.amazon[.]com/giftsredeemingrightnow
hxxps://www.amazon[.]com/giftsredeemingrightnow
 |
| Too late to say Sorry! |
When the link is clicked, we get Amazon's 404 page -- an image of a cute dog and a message saying “Sorry, we couldn’t find that page”. On the contrary, guess what happens? When you close the browser you will find that your files are encrypted. Unfortunately, we were not able to get our system encrypted as the installer checked registry keys for the presence of the virtual environment.
After not being able to accomplish my mission, I checked virus total for extra information
MD5 of the Word Document - 2843a3b7805ffc7fd058b9fd744ec836 [VT result]
Of course, the Word document was a downloader, but the file that was download was indeed malicious.
MD5 of the NSIS installer named 'Sys_Driver' - 766169d508d0eee096e07619c2a1416a [VT results]
 |
| VT results 10/57, CryptoLocker |
When we reviewed the malicious file on Virus Total, contradicting results were found. On one side, the AV vendors classified it as Cryptolocker. On the contrary, when I checked the comments section, one user has posted it to be Nymaim. We believe this is due to targeting, where the same URL may drop different malware depending on the visitor. Hence, I thought to probably avoid getting into the discussion of who is right, and leave it up to the discretion of the user to pick his side.
 |
| #Nymaim in the comments section |
While CryptoLocker is unlikely - it hasn't been seen in some time - we don't want to contradict the AV vendors until we can execute the malware ourselves.
Hopefully, this will widen up the eyes of Amazon and the individuals who have the authority to take action. Eventually, taking appropriate measures to cause damage to the threat actors. Beware American friends.
Stay tuned for latest updates on the Kelihos botnet in the coming future.












